UPDATED
 In case you haven’t heard, the Blaster worm has made some serious headway. We’ve seen dozens of computers in the last few days affected, with a variety of symptoms, from email not being sent out to the common system restarts. Wild stuff…
In case you haven’t heard, the Blaster worm has made some serious headway. We’ve seen dozens of computers in the last few days affected, with a variety of symptoms, from email not being sent out to the common system restarts. Wild stuff…
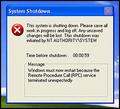
Weird confluence of bugs (did I just say confluence?) today. Guy drops off his laptop; it persistently, while he’s online with RoadRunner cable, shuts down, alerting him with a message about some RPC service error needing to quit… I plug his computer into the network to run Windows update, and another computer gets the same shutdown message… 15 minutes later we get a call from someone with the SAME problem… God Bless You Microsoft.
RPC stands for Remote Procedure Call (a standard method for implementing web-services), and as it turns out, the Microsoft implementation of RPC in Windows XP (and 2000 and NT, and anywhere else for that matter) is fatally flawed– anyone who can see your IP address can send a malformed RPC message and cause a buffer overflow and potentially gain access to your computer. Or, as was the case today, cause the RPC service to fail, and instigate the default Windows XP behavior of restarting the system [which can be altered by right clicking on My Computer>Manage…>Services].
Word on the street is, there’s a worm goin’ round that takes advantage of the RPC service in windows to f’ your computer up real bad.
The good news is that MS has patched the security flaw, the bad news is that almost no one goes to windows update on a regular basis.
The further bad news is that if you are online, and you’re a target of this exploit, it’s really difficult to go to the windows update site, because you’re constantly being restarted!
Some helpful hints:
- Disconnect from the network. Sort of obvious, but this will allow you to work unadulterated.
- Turn the Windows XP firewall ON on your primary internet connection. This will block the common ports that the RPC exploit runs on…
- Go to the windows management console. (right click on My Computer, choose Manage…, and then choose Services. Find the RPC service set it to Restart Service instead of Restart Computer in case of error [I’m not on a windows box right now so I can’t walk you through this process as precisely as I’d like!] This will keep your machine from shutting down if the RPC service should crash. WARNING: this might potentially make you more vulnerable for backdoor kind of attacks, since your computer remains alive and available for a hacker/worm to take advantage of. But I don’t know, I’m really just guessing here…
- Restart in Safe Mode with Networking (restart, holding the F8 key as your system boots. The previous steps may or may not be superceded by this step. consider them cautionary and couldn’t-hurts.
- Go to thewindows update site and download all the security updates there are.
Hope that works. The speed with which this particular problem has spread is really fascinating. The sad thing is that it’s so easily stoppable, if only Windows did a better job of keeping you up-to-date.
The little pop-ups that remind you “There are new updates for your computer” are pretty much useless, because they’re easily disabled, they’re not detailed enough, and (thanks to the prevalence of Messenger spams and banner ads which say “Your Computer is Not Up to Date!”) they’re hard to take seriously.
Moreover, something like this will go unnoticed by Norton Anti-Virus and it’s ilk, because it’s not a Virus, but it’s overall effect is similar. Let this be a caution to everyone — visit windowsupdate.com regularly.

thanks for your advice, this worm has been driving me mad
Glad to be of assistance — it’s a real bitch, this one. I should have put a #6: “Get a Mac.” heh.